
Most critical GPO misconfigurations in Active Directory
Group Policy Objects (GPOs) are a double-edged sword in Active Directory. They’re designed to enforce security and[…]

Offensive Security in Active Directory: Top 5 Risks and Pentesting Tools
Active Directory (AD) is the heart of identity and access management in most enterprise Windows environments. It[…]

How to root Android 12 (Google Pixel 3a)
Let’s see how to root an Android phone with a rooted Android from the official image, first[…]
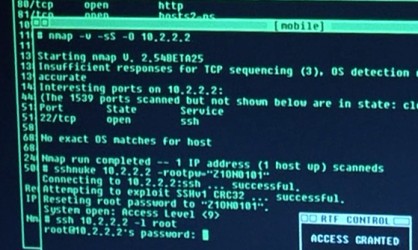
What is Penetration Testing?
A penetration test, colloquially known as a pentest or as ethical hacking, is an authorized simulated attack performed to evaluate the[…]
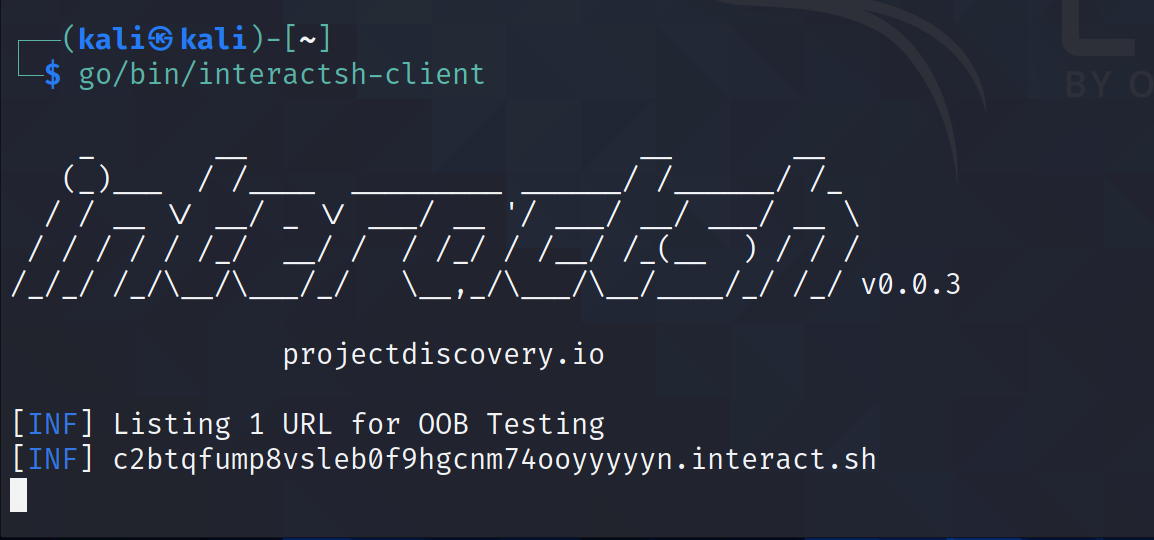
Interactsh: Open-Source OOB solution for SSRF, Blind SQLi, … in Kali Linux
Project Discovery, the same people behind Nuclei scanner that allows you to customize vulnerability scanning from YAML[…]